Proven Security Model
Since the beginning of the Internet, digital security has existed in the form of a public/private key system. This encryption-based security model is used worldwide to protect everything from your credit card when shopping online to online banking.
We take it much further.
Beyond Bank-Level Security
Tried and Tested Security Model
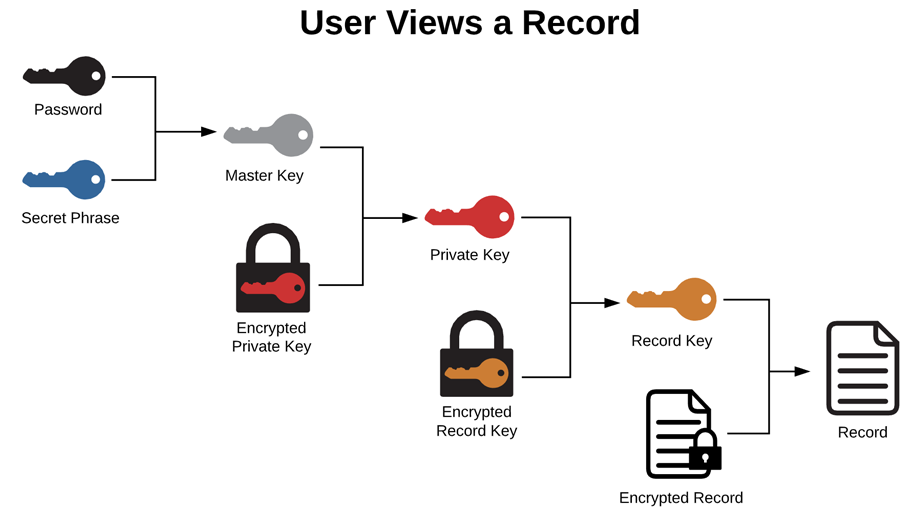
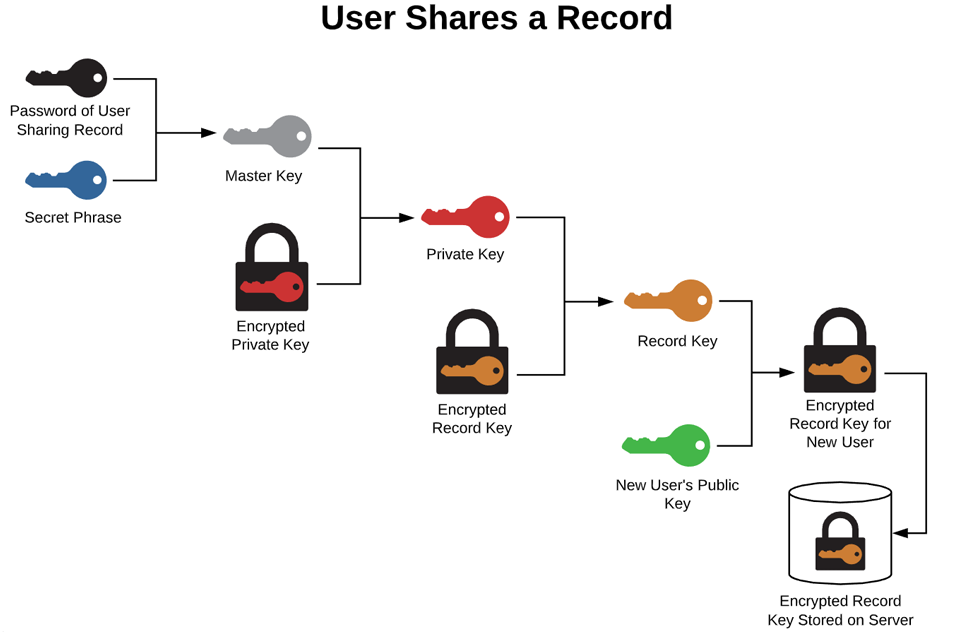
There is only one way to ensure your passwords are secure, and that is through the Zero-Knowledge Host-Proof Hosting model, which is the basis of Techferno's security. All of your sensitive data is encrypted and decrypted only on your local computer. When the data leaves your computer, it is encrypted several times over and only you hold the key (the combination of your password and secret phrase) to unlock it. Not even the expert developers at Techferno can access your secure data.

A hacker's worst nightmare
Should someone get access to your data, multiple layers of cryptographic hashes and encryption thwart any attempt to read it.
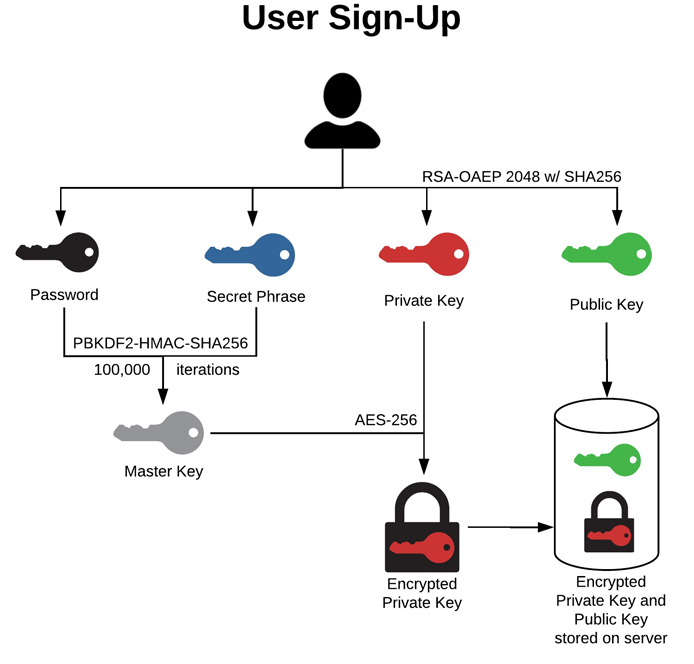
Master Key: Your password and secret phrase are used to create an irreversible hash - the Master Key.
Encrypted Private Key: The master key is used to encrypt your private key.
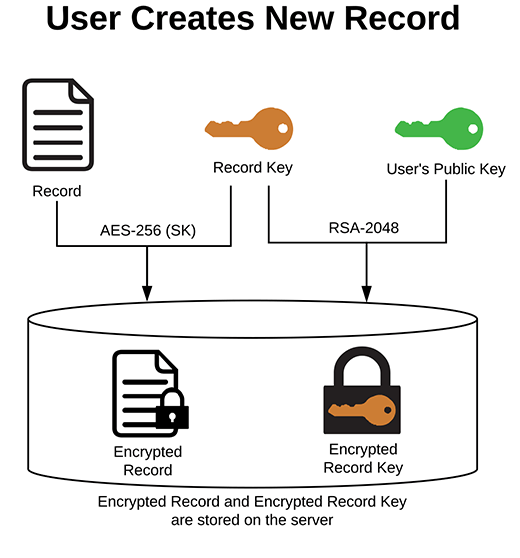
Encrypted Record Key: The record key is uniquely generated for each record and encrypted using your public key that can only be decrypted with your private key, which as mentioned above, is encrypted with the master key.

Secure Remote Password
Utilizing the Secure Remote Password protocol (SRP6), the password you enter to log in is never actually transmitted. Instead, your password is converted into a complex key that can only be used once.
This means that even a weak password becomes impossible to decrypt and even if someone were to break the unbreakable encryption of an SSL certificate and obtain that key, it would do them no good because it can't be used again.

Brute Force Protection
We use PBKDF2-HMAC-SHA256 with 100,000 iterations to protect your data against brute force cracking. It would take 100 billion computers 100 octillion years to break the encryption of your combined password and secret phrase, which is over 128 bits of entropy.

A+ Rated 256-bit SSL
We use an A+ rated SSL certificate to encrypt the transmission of data between our server and your computer.

2-Factor Authentication
2FA is available for you to enable to provide another layer of security to your account. 2FA combines your password (something you know) with your phone (something you have). While 2FA has gained in popularity over recent years, it has actually been used by enterprises for decades to allow remote access to sensitive systems and has proven to be an effective additional layer of security for accessing remote data.

How exactly does it work?
View the diagrams below to see how the processes work behind the scenes.
Tap to zoom.