Every day we’re entrusting more of our personal data to the cloud. From social media, to video, scheduling, data backups, and even our current location, integrating ourselves with the web has become a way of life.
However, there’s an increasing awareness that companies, governments, and bad actors routinely gain access to our most sensitive information without our consent. Data breaches are a common headline. Even major technology providers – those we’re relying on to facilitate our emails, photos, and daily comings and goings – are routinely scrutinized for misusing or abusing private information stored on their servers.
With a growing dependence on the cloud, how can we trust that our information will be safe? There is no single “silver bullet” for this complex and multi-faceted problem, so we must take a multi-layered approach to achieve the ultimate in data security – zero-knowledge software.
Encryption
When it comes to securing highly sensitive data, the most important tool at our disposal is powerful encryption. With strong encryption, we can scramble information in such a way that renders it useless to anyone who doesn’t hold the key to unscramble it. This has led to government-run security agencies around the world, stymied by encryption, to push for laws that grant backdoor access – further validating the strength of powerful encryption.
Zero-knowledge software uses encryption in several important ways.
End-to-End Encryption (E2EE) (transmitting data securely)
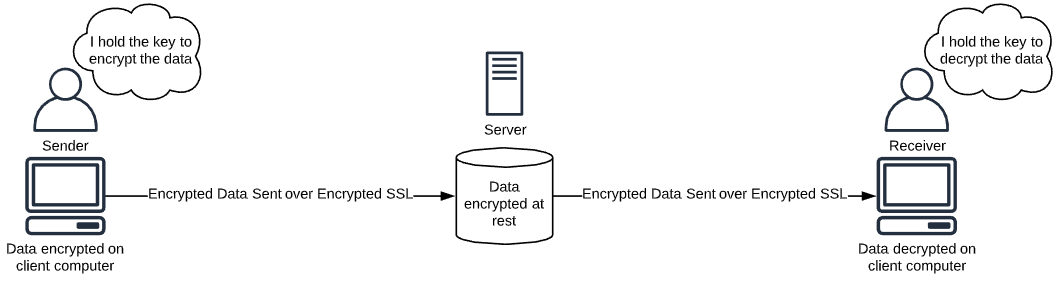
End-to-end encryption, or E2EE, is the process of encrypting data on the sender’s device and decrypting it at the receiver’s device. In the case of messaging apps, your message is encrypted on your device and decrypted on the device of the person you are sending the message to. For a password manager, both ends are often the same computer – your computer that you are using to save and retrieve your passwords.
Isn’t this what an SSL does?
End-to-end encryption is often incorrectly associated with SSL certificates, or “https.” While an encrypted connection adds another layer of security that all software providers should use, it is not a core component of zero-knowledge software. This is because the encrypted SSL connection is decrypted when it reaches the server. As such, the server now has knowledge of the data transmitted to it. In fact, an SSL connection should properly be called “point-to-point encryption” because the connection is encrypted between each point, not one continuous encrypted connection between each end of the data being sent and later received by the user(s).
Although an SSL connection is a great thing to use for everyday internet use, like email and online shopping, it cannot be relied on in an environment where you want to ensure no one except you can access your data.
Ultimately, true end-to-end encryption isn’t enough, because even though your data is encrypted, the questions become, how is the data being stored and who has the key to decrypt it?
Encryption at rest (storing data securely)
“Encryption at rest” is when information is stored on a server in an encrypted format. Although not all information in the cloud needs to be encrypted at rest, some information should, such as Protected Health Information (PHI) and sensitive data like financial information and passwords. This means that even if an attacker were to obtain the data from the server, it would be encrypted and unreadable.
Strong end-to-end encryption and encryption at rest allows you to transmit and store your data anywhere without fear of it being compromised. It’s like creating an impenetrable protective bubble around your data. It’s free to safely travel on potentially dangerous roads and rest at ease – even living among thieves.
As great as this sounds, encryption is no guarantee that your data remains private because it’s still dependent upon who can unlock it. Service providers (hosts) often hold the keys to unlocking your scrambled information, and whether they’re keeping those keys safe is another question. Wouldn’t it be great if we didn’t have to trust the host?
Host-proof hosting (limiting access to the key)
The use of encryption across the internet typically involves more than one person holding the key to decrypt the data. A common example is where popular data backup providers, such as Backblaze, Carbonite, and Dropbox have access to your encryption key in order to provide enhanced services, like the ability to view your files online from any computer. This functionality can only be achieved and offered if the host has some way to access your key to decrypt your data. Thus, this is not host-proof hosting.
These same services do offer an option to enable a host-proof hosting model by using your password as the key; however, just like password managers that use this model, if you lose your password, you lose the ability to decrypt your data. As this puts more responsibility on the user, this is not the default option for these data backup providers.
Password managers that have properly set up host-proof hosting never have access to your key. For you to access your data, you must first download it, and then decrypt it. If your data is decrypted anywhere other than your local device, that means that someone else could potentially obtain your key.
Secure Remote Password (SRP)
A major component of limiting access to your key is SRP. SRP is used to authenticate you with the server in order to grant you access your encrypted data without revealing your password to the server. This is important because even if the server doesn’t hold the key, if it’s revealed to the server in any way, such as during the log in process, then the host has the ability to obtain your key and decrypt your data.

Don’t be fooled
When a software/service provider throws around terms like “strong encryption,” “end-to-end encryption,” and “encryption at rest,” it doesn’t necessarily mean that your sensitive data is safe. While these are important measures, they are merely building blocks towards achieving security. The secret sauce is combining all these techniques in the right way, culminating in zero knowledge, host-proof hosting.
By starting with end-to-end encryption, we can prevent anyone unauthorized from accessing your information during transit. Then encryption at rest makes your data invulnerable to data theft. And host-proof hosting limits access to the key only to you. So, a “zero-knowledge provider” is a service that is designed to take advantage of all these technologies to create an environment impervious to hacking and cracking.
