Your password separates an exhausting list of personal data from unscrupulous individuals who can turn your life upside down. Bank accounts, private emails and entire businesses are often protected by one important string of characters.
But how do you defend yourself from the constant threat of data theft? By knowing what tools and techniques they use! When you know how common password cracking methods work, it’s easier for you to create a strong password.
What Is Password Cracking?
Often mistakenly referred to as “hacking,” password cracking refers to methods and tools used to reveal a user’s password. For most cases, password cracking is an elaborate guessing game, primarily using specialized software and one or more powerful computers.
The difficulty of cracking a password depends on the specific password cracking methods used and, most importantly, the password or passwords being targeted.
Who’s Vulnerable to Password Cracking?
Everyone who has a password. Everyone from CEOs of the largest corporations to your great aunt who’s only experience with a computer was creating a Facebook account she hasn’t logged into for years can be targeted or have their passwords included in a mass digital attack.
If you have an account on any website, there are likely people out there who want access to it. Sometimes it’s for monetary gain, sometimes it’s for blackmail, and sometimes it’s simple, but criminal curiosity.
The biggest targets tend to be websites that store your personal information. When your accounts are breached here, they can be used to access other accounts. Email accounts are one major target, however, any site with weak security that can be used to discover your password can leave your vulnerable if you refuse passwords on other sites.
While everyone is a target, criminals out for profit often prefer to target victims who will have a higher chance of having important data, particularly businesses. Obtaining information from a business can open the doors for targeted fraud and theft that can cripple a business and be nearly impossible to track.
Ultimately, if you’ve ever created a username and password for any website, software or internal office utility, you’re at risk.
What Are the Most Common Password Cracking Methods?
While the science and technology behind cracking passwords changes almost daily, there are categories of cracking that help divide and explain the base concepts behind each method. Here are the most common password cracking methods likely to be used against you right now:
Dictionary Attacks

Think of every password you’ve ever created. If you thought of it on your own, chances are it’s a word or two, maybe with some variations and extra characters. Password crackers know this – most people prefer to create their own passwords using words that are important to them and easy to remember.
Unfortunately, there really aren’t very many words. The English language currently has around 170,00 words total. You can add in proper nouns and common words borrowed from other languages, but that still isn’t very many – to a computer.
Dictionary attacks use pre-set dictionaries to try the most likely character combinations you’ve used in your password. This doesn’t mean it only uses literal dictionary words, though that would be one, albeit broad, option. Instead, dictionary attacks allow a cracker to import and customize a list of words and set rules to attempt only the most likely combinations. All of this is done automatically with computer software which can fly through billions of potential combinations per second!
While they may start their dictionary with all known English words, they will then refine their tool. In addition to targeting common words, dictionary attacks can add prefixes or suffixes with common additions like exclamation marks or numbers, try substituting letters for obvious alternatives like “$” instead of “S” and dozens of other variations.
Dictionary attacks are especially powerful for their ability to be targeted. If a celebrity is being targeted, crackers can obtain information from all over that may contain likely base words for a password such as pets, family members, home addresses, dates of birth and more.
This is one reason why a core part of maximizing your password entropy is randomness. While the average person is unlikely to be targeted, the more your password is associated with people or things in your life, the easier a target you are.
Brute Force Attacks

Dictionary attacks are sophisticated, customizable and often targeted. On the other hand, the same technology used in dictionary attacks can be applied in a much more broad and unfocused attack. Instead of starting with base words and exceptions, a password cracker could simply let software run that tries every variation of characters possible. This is known as a brute force attack.
Brute force attacks aren’t as common as they used to be, primarily because of how much easier it is to use or create software based on the more successful dictionary style of attack. However, they’re another tool in a cracker’s repertoire that could be used when time isn’t a factor and their resources are greater.
The benefit of a brute force attack is that it can technically crack completely random passwords. Imagine trying to dial every phone number starting with 000-0000, then moving to 000-0001. There are a lot of combinations (around 10 million, without counting area codes.) Brute force attacks work just like this and run as long as the cracker’s computers allow them to.
Brute force attacks can technically guess any password, but time works against them. Most websites require a minimum character limit and the addition of special characters which, if you aren’t using commonly cracked passwords (like “password123”) would theoretically take centuries or millennia for modern computers to guess.
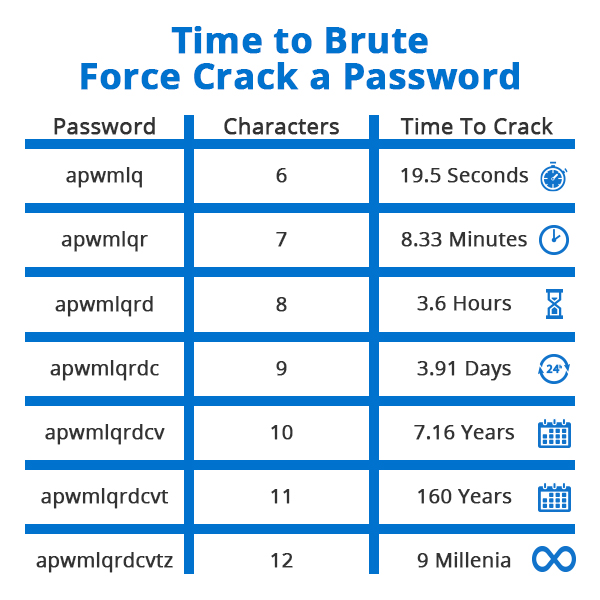
These examples don’t include mixed case or special characters, but you can
still see how quickly the time to crack them increases. Simply put, if your
password is an appropriate length and complexity, it’s statistically impossible
for it to be guessed in our lifetime or many more after it.
Keyloggers
Not all password cracking attempts use a guessing system. Others use malware like keyloggers, software designed to track every keystroke you make and send that data back to the intended password thief. When keylogger software is installed, a file is created that logs every single time you type on your keyboard. At set intervals or even in real time, that data is sent back to the source that installed it on your PC.
Keyloggers are threatening in that no matter how difficult your password is, the software doesn’t need to guess – it just waits for you to type in private details. They also introduce a variety of other security issues, such as compromising messages you send, even if you thought you were sending them over secure channels.
The biggest hurdle for keylogging software is installing it on a target PC. Practice safe behavior on the Internet and your chances of being keylogged decrease dramatically. Don’t open attachments you weren’t expecting, don’t download files from websites you aren’t familiar with and never plug random USB drives into your computer or laptop.
Are There Other Ways to Discover Passwords?
Of the common password cracking methods, automated software is typically the standard. The ability to mass deploy attacks or instantly change targets makes it able to cast a wide net effortlessly. But that doesn’t mean your passwords are only under attack from cracking software.
Large companies, notable figures and businesses that are known to store a lot of data, like IT firms and advertising agencies, are targets for more uniquely targeted attacks:
Social Engineering
Password security, like most things, is only as strong as the weakest link. In many cases, the weakest link is a friendly, welcoming person. Social engineering, in security terms, describes a malicious form of manipulation designed to gain access to data or information by exploiting everything from expectations to politeness.
For example, a very basic type of social engineering for those looking to access data is to play the role of an IT specialist. They can either reach out to you over the phone or show up in person. They’ll describe how they were contracted to help resolve a technical issue and just need access to your server room or remote access to a company PC. In an attempt not to disrupt a critical repair, a staff member may let them through without asking any questions.
Once they’ve reached their goal, they can begin using other tools to breach a security system and install malware, like keyloggers.
Social engineering can be digital too. If a cracker spoofs an email account to look like it came from a friend or coworker, you may be tricked into giving them information you would never share with someone outside your business.
The best way to fight social engineering is to have strict security guidelines and train employees how to handle these situations. Social engineers prey on friendliness, so it’s important to remind staff that security guidelines exist for a reason, and not to feel insulted or distrusted if coworkers won’t share information that could be a breach of security.
In-Person Theft
Especially when it comes to passwords, sometimes there’s no “cracking” that needs to be done at all. Offices across the globe are full of sticky notes, notepads and big whiteboards with passwords and other sensitive information right now.
It doesn’t take a genius password cracker to remember a simple password they saw stuck to your monitor. We often think of password attacks as purely digital – but they can take place in the real world if you leave your guard down.

You can combat in-person password theft easily. A password manager removes the need for sticky notes or password sheets stored at your desk. Even sharing passwords becomes easy with a password manager that allows for individual record sharing, like Techferno password manager.
If you must use sticky notes, just remember to keep them out of plain view. Most in-person data thefts are crimes of opportunity.

Protect Your Passwords with a 14 Day Free Trial
Want to use the strongest passwords possible without the stress of remembering them? Techferno stores an unlimited number of passwords and other sensitive information, protected by a unique system of secure layers to keep them safe.
Designed for agencies, IT companies and any other business that manages several passwords, Techferno allows you to share access to passwords and more while retaining the protection of our state-of-the-art secure platform.
Sign up for your 14-Day Free Trial today!
